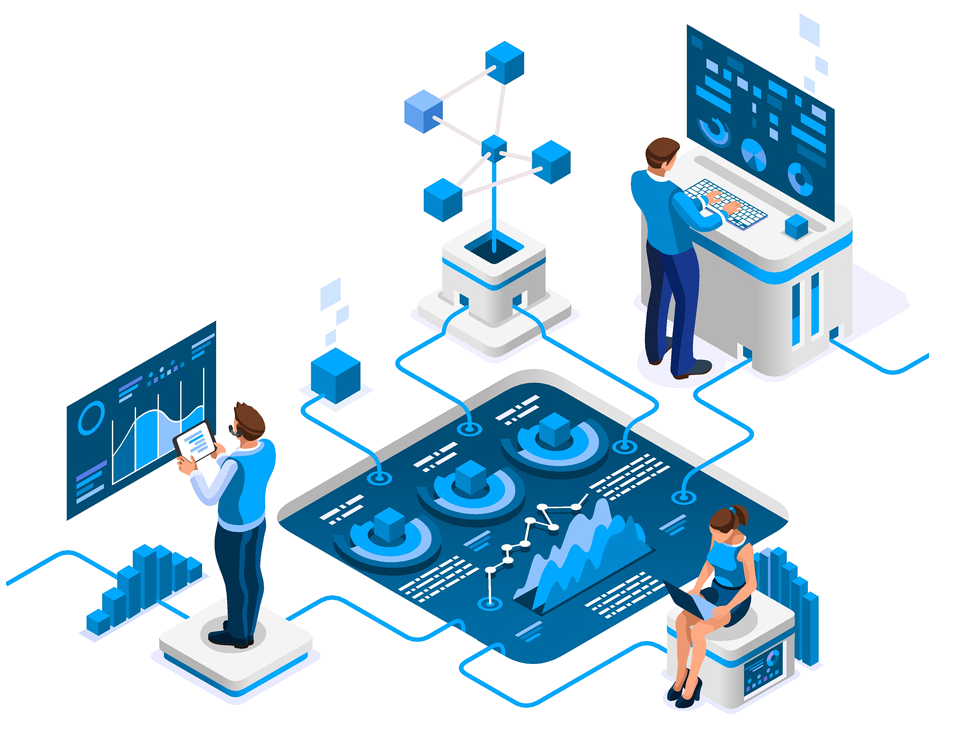
Monitoring the internet at a global scale.
We have a multi-cloud globally distributed sensor network that provides unique data streams into our aggregators.
Active and Passive monitoring at a global scale.
We have a multi-cloud globally distributed sensor network that provides unique data streams into our aggregators.
Sensors are running globally in distributed cloud environments. They run a random honeypots from a curated list watching for specific attack vectors or threats to those running sensors. They are ephemeral by design, eventually expire and a new pseudo-random sensor is created to continue collecting.
Other data is collected and openly sourced from a variety of sources.
All collected data is coalesced, de-duplicated, and de-noised modeled into a curated attack-based threat intelligence feed that products are able to utilize with minimum memory overhead and minimum CPU processing. Currently our sensors and aggregation work in real-time and the updated models are sent down to existing products every hour; way above indrustry standard for threat protection.
When an attack is blocked by our products, that information is sent in real-time to your management portal. It is collected and used as part of a feedback loop into our attack modeling systems. This can be helpful in identifying trends in active campaigns or thresholds when attack-behavior activity spikes.
Infrastructure deployments trusted with






We model attack behavior on the Internet at a global scale. We have strategically deployed sensors that automatically self-destruct and create new listeners on random time intervals as part of our monitoring system. This data is analyzed with other intelligence sources, coalesced, de-duplicated, and modeled to create a unique detection and as part of IOTD's protection. This allows our products to block instantly, on first packet, and locally without having to send any private meta-data to our cloud!
The sensor collectors will stream data over to our queueing processors in real-time of a secure tunnel (from the sensor to the collector). Daily we do domain zone harvesting looking for DGA (Domain Generation Algorithm) techniques, domain kiting, short-lived domains with recurrence patterns in order to provide protection at a domain resolution layer. In addition our long-running sinkhole data is aggregated with the active sensor collection. All data is modeled to present the attack-based threat intelligence data available at any time. Currently we send this down to our subscribers hourly.